Gästbloggare Derek Melber, Active Directory MVP, berättar om hur organisationer kan identifiera avvikelser genom att upprätta en "baseline" av normala aktiviteter specifika för varje enskild användare och därefter övervaka och spåra ovanlig filaktivitet hos användare.
In this blog, we’ll look at how organizations can track users’ unusual file activity. But first we take a look at how we identify anomalies by establishing a baseline of normal activities specific to every single user.
Cyberthreats are on the rise and breaches are becoming more common. Many businesses rely on technology to protect themselves, but attackers also use technology to find ways to get around these defenses. With artificial intelligence making its way into the technology space, businesses need to be well-equipped to incorporate this new security technology.
Prevailing challenges in threat detection
Insider threats continue to be a challenge for businesses of all sizes; one way to detect them is by establishing a baseline of normal activities specific to each user over an extended period of time and then monitoring for any deviations from that norm. However, it’s nearly impossible to manually detect these deviations.
Another area of concern is false positive alerts, which are a source of distraction that delay breach detection. False positives can be reduced by setting thresholds specific to each user based on their level of activity rather than using a blanket threshold across the organization, but this still remains a task that’s impossible for IT security professionals to manually perform.
User behavior analytics (UBA)
ADAudit Plus uses machine learning to create a baseline of normal activities that are specific to each user to detect potential insider threats and notify the concerned personnel. UBA in ADAudit Plus helps IT security teams streamline threat detection by creating a behavior-based security ecosystem to detect threats.
UBA combines data analytics and machine learning to define dynamic thresholds based on real-world user behavior. With its alert thresholds, ADAudit Plus reduces the number of false positives, giving security teams plenty of time to focus on the real indicators of compromise.
Tracking unusual file activity count
Consider a scenario where a disgruntled employee departing from the organization decides to steal critical financial information. If this user, who normally accesses ten documents a day, goes on to copy a hundred documents, that’s a clear sign of serious abnormality and warrants immediate attention. An auditing solution that doesn’t use UBA would consider this normal file access and activity, thus not triggering any alerts. However, this is a clear case where the user’s activity is abnormal and UBA would trigger an alert.
ADAudit Plus in conjunction with UBA tracks all abnormal file access behavior for all users in a domain. To track users’ unusual file activity in your organization, follow these steps:
- Log in to ADAudit Plus.
- Click Analytics to view the summary of all anomalies, as shown in Figure 1.
- Under the list of activity types, select Unusual Activity – File Activity Count (Based on User) to view the detailed report. See Figure 2.
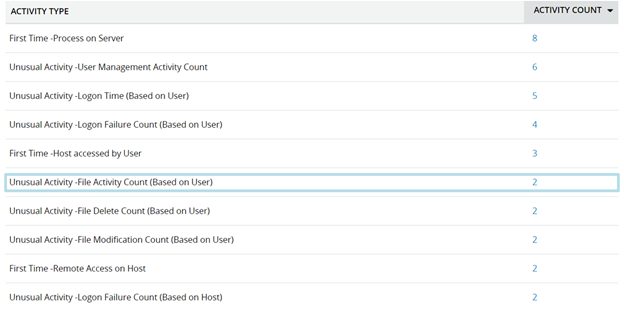
Figure 1. Summary of unusual activities.
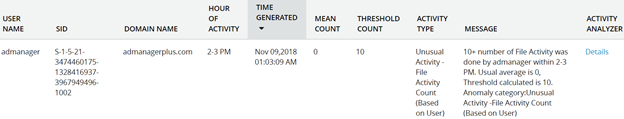
Figure 2. Monitoring unusual file activity count using UBA in ADAudit Plus.
Having a report of the activity is nice, but most administrators don’t have time to review reports. By default, ADAudit Plus’ UBA alerts trigger an email notification. You can also configure these alerts to be sent via SMS. To edit alert profiles, follow these steps:
- Select the Configuration tab.
- Go to Alert Profiles > View/Modify Alert Profiles. Select the profile named Unusual Activity – File Failure Count (Based on User).
- Click Configure to modify the alert profile. You can choose to be notified by email, SMS, or both. See Figure 3.
- Click Update.
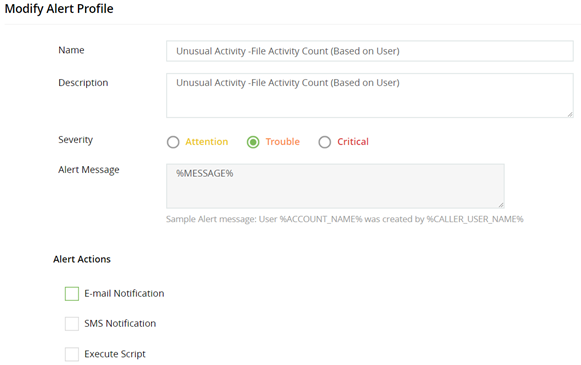
Figure 3. Configuring an alert profile.
Once you’ve configured these settings, you’ll receive an alert when users have unusually high file activity counts.
Summary
UBA solutions have superior threat detection capabilities and can help administrators deal with both rogue users and compromised accounts. These advanced features make UBA an important part of any organization’s security framework. ADAudit Plus’ UBA engine helps monitor user activity for instances of unusual activity. If a user’s activity count exceeds the threshold value that was calculated based on their normal behavior, ADAudit Plus triggers an alert to draw administrators’ attention so they can take immediate action. 